Biometrics can be defined as measurable physiological or behavioral characteristics used to verify an individual’s identity. These include fingerprint recognition, hand geometry, retinal and iris scanning, face recognition, and signature verification.
The term biometrics (or biometry), also known as a biometric characteristic or biometric trait, refers to the scientific study of “life measurement.” It originates from the Greek words bios (meaning “life”) and metron or metrikos (meaning “measure”).
Biometric research expands on this definition, describing biometrics as the automatic identification of individuals based on their physiological or behavioral traits. According to Biometric Research (2003), a biometric system is essentially a pattern recognition system that determines a person’s authenticity by analyzing specific physical or behavioral characteristics.
Biometrics serves as a general method for identifying or authenticating individuals, ensuring they are who they claim to be. While initially reserved for high-security applications, biometrics is now widely used in public-facing sectors, including prison visitor systems, driver’s licenses, canteen administration, benefit payment systems, border control, voting systems, and school security.
According to Ashbourn, future biometric applications may extend to ATM authentication, workstation and network access, travel and tourism, online transactions, telephone banking, and public identity cards.
A Brief History of Biometrics
According to Ashbourn (1999), personal identification numbers (PINs) were among the first automated recognition identifiers. However, these systems recognized only the PIN itself rather than verifying the identity of the person using it. The same limitations apply to cards and other tokens, which can be lost, stolen, or misused. While combining a PIN with a card or token provides a slightly higher level of security, it remains vulnerable to compromise.
In contrast, biometric identification offers a unique and non-transferable method of verifying an individual’s identity, making authentication more accurate and streamlined. Although it is tempting to think of biometrics as a futuristic technology, Ashbourn (1999) points out that the fundamental principles of biometric verification have been understood and practiced for centuries.
For instance, thousands of years ago, people in the Nile region routinely used biometric verification in everyday situations. They identified individuals based on distinct physiological features, such as scars, physical measurements, and a combination of traits like complexion, eye color, and height. While they lacked automated biometric readers or computer networks, the underlying concept of identity verification was remarkably similar to modern methods.
In the 19th century, researchers sought to correlate physical characteristics with criminal tendencies, leading to the development of various measuring devices. Around the same time, fingerprinting emerged as a widely adopted method of identity verification among police forces worldwide. Although the absolute uniqueness of fingerprints has been debated, it remained the most effective identification method and continues to be the primary tool for law enforcement agencies.
Given this historical background, it is unsurprising that the potential for using electronics and microprocessors to automate identity verification has long fascinated individuals and organizations in both the military and commercial sectors. Over time, various biometric projects were initiated, including the development of an early hand geometry reader—a large and cumbersome device that was later refined into a smaller, more efficient version, becoming one of the early pillars of the biometric industry.
Simultaneously, other biometric technologies, such as fingerprint verification, continued to evolve, becoming increasingly reliable and accessible. In recent years, there has been growing interest in iris scanning and facial recognition, which offer the advantage of non-contact identification. However, these technologies also introduce new challenges that must be addressed.
Over the past decade, the biometric industry has matured significantly. What once consisted of a handful of niche manufacturers struggling for adoption has transformed into a global industry, shipping biometric devices in substantial volumes. With the emergence of large-scale applications, the industry is now poised for significant growth (Ashbourn, 1999).

Clarifying Certain Terms
Verification
Verification is the process of confirming or denying an individual’s claimed identity—”Am I who I claim to be?” Most biometric devices operate in verification mode, where an individual claims an identity by retrieving a stored biometric template from memory. A live sample is then captured and compared against this template to determine a match or no match based on predefined parameters.
Verification is essentially a one-to-one comparison, allowing for a quick and binary yes/no result. According to Prabhakar et al., verification involves validating an individual’s identity by comparing their captured biometric characteristic with the pre-stored biometric template in the system’s database.
Identification
Identification involves establishing an individual’s identity—”Who am I?” It can be seen as the process through which a real-world entity is recognized, and its identity is confirmed. While most biometric systems operate in verification mode, only a few claim to offer biometric identification. In this case, the individual submits a live sample, and the system attempts to identify the individual by comparing the sample to a database of templates.
Identification is a more complex one-to-many comparison, which may produce multiple results depending on the number and similarity of the stored templates. Put another way, a new biometric measurement is compared against a large database containing information about many individuals. This means that the system identifies the individual’s presence at a specific location and time, based on the transaction or data provided.
Authentication
Clarke defines authentication as the process of establishing a degree of confidence in the truth of an assertion. In biometric authentication mode, the system verifies an individual’s identity by comparing a trial template, generated from a live sample, to a reference template stored in the system. This is known as a one-to-one (1:1) matching process.
Simply put, a new biometric measurement—claimed to belong to a specific individual—is compared against the corresponding stored data. Authentication is commonly used to verify an individual’s identity before performing a specific action, such as gaining access to a building or retrieving sensitive data.
According to Allan, biometrics offers a significant advantage over other authentication methods because it enables identity verification without requiring the individual to enter an identifier, such as a username or password. Instead, the system automatically recognizes the person based on their unique biometric traits.
Recognition
According to Allan, in recognition mode, a biometric system combines identification into a single-step process. The system determines an individual’s identity by matching their biometric sample against multiple stored templates. This is known as a one-to-many (1:N) matching process.
How Do Biometric Systems Work
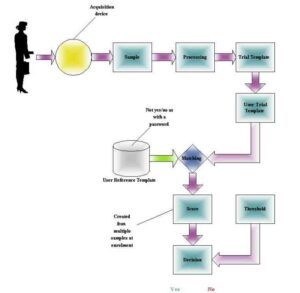
According to Allan (2002b), while biometric technologies differ in what they measure and how they measure it, all biometric systems follow a similar process. This process can be summarized in the following steps:
- The individual submits a biometric sample—an identifiable, unprocessed image or recording of their physiological or behavioral traits—to an acquisition device, such as a scanner or camera.
- The biometric sample is processed to extract distinctive features, creating a trial template or verification template. This template consists of large numerical sequences, making it impossible to reconstruct the original biometric sample. It functions as the individual’s unique “password”.
- Verifying a memorized password or a one-time password (OTP) generated by an authentication token is a simple yes-or-no decision. However, verifying a trial template is more complex. The trial template is compared against a reference template or enrollment template, which was created using multiple biometric samples during the individual’s initial enrollment in the biometric system.
- No two biometric templates are ever identical, so the system must determine whether there is a “close enough” match by checking if the matching score exceeds a predefined threshold.
- Therefore, the accuracy of a biometric system is measured by:
- False Match Rate (FMR) / False Acceptance Rate (FAR): A lower FMR indicates better security in a biometric identification system. FMR refers to the incorrect matching of biometric measurements from two different individuals, mistakenly identifying them as the same person.
- False Non-Match Rate (FNMR) / False Rejection Rate (FRR): A lower FNMR improves the ease of use of a biometric identification system. FNMR occurs when biometric measurements from the same individual are mistakenly recognized as belonging to two different individuals, leading to an incorrect rejection.
Biometric Methodologies
This section discusses two different biometric methodology categories, namely physiological biometrics and behavioural biometrics. The section further lists some strengths and weaknesses, as well as suitable applications per biometric methodology as summarized by Allan.
Physiological biometrics
Physiological biometrics, also called physical biometrics or static biometrics, is based on data derived from the measurement of a part of an individual’s anatomy.
- Currently, there is a greater variety of fingerprint verification approaches available than any other biometric method. These approaches include emulating traditional police methods of matching minutiae, straight pattern matching devices, and even systems capable of detecting whether a live fingerprint is presented.While fingerprint devices can achieve high accuracy (with low false acceptance rates), they can still face usage errors, especially among insufficiently disciplined users, leading to higher false rejection rates, particularly in large user bases. The user interface and its performance in larger-scale usage across diverse environments should also be considered.According to Allan, it has been established that the likelihood of two individuals having the same fingerprint is less than one in a hundred billion. Fingerprints form in the womb at around five months and remain unchanged even after death. In fact, fingerprints have been successfully recovered from well-preserved mummies over two thousand years after their death.
- Hand geometry, as the name suggests, involves measuring the physical characteristics of an individual’s hand and fingers. This method provides a good balance of performance characteristics and is relatively easy to use.According to Ashbourn, hand geometry may be particularly suitable for larger user bases or for individuals who access the system infrequently, as they may be less disciplined in their approach to the system. The method offers high accuracy when desired, and its flexible performance tuning allows it to accommodate a wide range of applications. The ease of integration with other systems and user-friendliness make hand geometry a common first choice for many biometric implementation projects.According to Allan, virtually every individual’s hands are shaped differently, and this shape does not significantly change over time. A biometric template can be created from measurements of the geometrical characteristics of an individual’s hand.
- Retinal scanning is an established technology where the unique patterns of the retina are scanned using a low-intensity light source via an optical coupler, and it has proven to be highly accurate in practice. However, it requires the individual to look into a receptacle and focus on a given point. This may not be convenient for spectacle wearers or individuals with concerns about intimate contact with the reading device.According to Allan, alongside iris recognition technology, retinal scanning is considered one of the most accurate and reliable biometric technologies available.
- Iris scanning is considered one of the least intrusive of the eye-related biometric methods (Ashbourn, 1999). It uses a conventional CCD camera and requires no intimate contact between the individual and the reader. Additionally, iris scanning offers the potential for high template matching performance and has been shown to work well with spectacles and across a variety of ethnic groups. It is also one of the few biometric methods that performs effectively in identification mode.According to Allan, the uniqueness of eye identification is well-established. The iris is a robust biometric because it remains unchanged throughout an individual’s life and is not subject to wear or injury, although corneal damage, disease, or similar conditions may obscure the iris. The iris contains six times as many distinct identifiable features as a fingerprint.
- Face recognition is a technique that has attracted significant interest, but its capabilities have often been misunderstood. Over time, extravagant claims have been made about facial recognition devices, many of which have been difficult to substantiate in practice. While matching two static images may be straightforward, it is a much greater challenge to unobtrusively detect and verify the identity of an individual within a group. While the appeal of facial recognition is clear from an individual’s perspective, the expectations of the technology need to be realistic.According to Allan, an obvious limitation of face verification is that it generally disregards changeable characteristics like hair color and style, which means it cannot differentiate between monozygotic (identical) siblings. While facial recognition systems have had limited success in practical applications thus far, progress continues to be made. If the technical obstacles can be overcome, facial recognition could become a primary biometric methodology in the near future.
Behavioural biometrics
Behavioural biometrics, also known as dynamic biometrics, is based on data derived from measurements of an action performed by an individual. This type of biometric incorporates time as a key metric, meaning the action has a beginning, middle, and end. It focuses on how an individual behaves during a task rather than physical traits.
- According to Ashbourn, voice verification is an interesting technique, especially given the volume of voice communication that occurs during everyday business transactions. Some designs have focused on wall-mounted readers, while others have aimed to integrate voice verification into conventional telephone handsets.Allan states that while voice is generally less accurate than other biometrics, its main appeal lies in its suitability for telephone applications and interactive voice response (IVR) systems. One of the key advantages of voice verification is that it can be deployed without additional hardware costs.
- Signature verification benefits from a synergy with existing processes that other biometric methods lack. Individuals are already accustomed to using signatures as a means of transaction-related identity verification, making it relatively seamless to extend this to biometrics. Signature verification devices have proven to be reasonably accurate and are suitable for applications where signatures are accepted as identifiers.According to Allan, signature identification systems analyze two distinct areas of an individual’s signature: the visual features of the signature itself and the dynamic features of the signing process. These include characteristics such as speed, pen pressure, stroke length, and the moments when the pen is lifted from the paper. While someone may be able to replicate the visual image of another person’s signature with enough practice, it is difficult, if not impossible, to duplicate the dynamic features of the signing process.
Frequently Asked Questions
What is biometric authentication?
Biometric authentication is a security process that uses unique biological characteristics (such as fingerprints, facial recognition, iris scans, or voice patterns) to verify the identity of an individual. It is commonly used in smartphones, security systems, and financial services for secure access.
Which is best provider for biometric solutions?
KBY-AI provides customers with powerful biometric SDKs including face recognition, palm recognition, etc.
How secure is biometric data?
Biometric data is considered more secure than traditional password-based methods because biological features are difficult to replicate or steal. However, it is not foolproof, and concerns about data breaches and privacy exist, making it important to use strong encryption and secure storage for biometric data.
Can biometric systems be fooled or hacked?
While biometrics offer strong security, they can be vulnerable to certain attacks, such as spoofing (e.g., using a photo or a fake fingerprint). Security measures such as liveness detection, multi-factor authentication, and encryption can reduce these risks.
How is biometric data stored and protected?
Biometric data is often converted into a mathematical model or template rather than stored as raw data. This template is encrypted and stored locally on the device or on secure servers. Proper encryption, secure communication channels, and adherence to privacy regulations are key to protecting biometric data from unauthorized access.
Conclusion
Biometrics systems, while varying in their specific methods, all function in a similar way. It is essential to recognize that the ease of enrolment and the quality of the template are key factors in determining the overall success of any biometric system. Additionally, user perceptions concerning security and privacy are social factors that need to be addressed in order to facilitate user adoption when biometrics are used for electronic business identification.
It was concluded that biometric identification methods should be marketed as privacy-enhancing technologies (PETs), emphasizing their role as privacy protectors rather than as privacy invasion technologies. This approach would help gain trust and acceptance among users, highlighting the security benefits without undermining personal privacy concerns.


